ADFS/Office 365 SSO 80041034 Error
Recently after configuring Active Directory Federated Services for a customer for Azure AD Premium/Office 365, we received the following error while testing user login to https://portal.office.com:
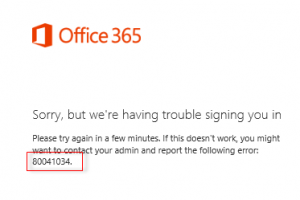
Sorry, but we’re having trouble signing you in.
Please try again in a few minutes. If this doesn’t work, you might want to contact your admin and report the following error: 80041034
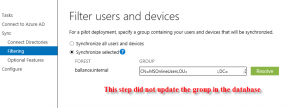
The obligatory Google search showed potential fixes relating to cached ADFS entries for users post-UPN changes (which we had done as a prereq. for MS Online Services). We ran the LsaLookupCacheMaxSize fix here: https://support.microsoft.com/en-us/kb/2535191. This did not resolve the issue. The other suggestions found online were to convert the MSOL Domain from Federated to Standard and back again. While I’m sure this would have helped, the easier option was to remove the Relying Party trust from ADFS:
Followed by running the Update-MsolFederatioDomain -DomainName ourexternaldomain.co.nz
![]()
This then placed an updated/correct copy of the Relying Party trust into our ADFS server which resolved the issues!